The American public has not been told the whole story of Epstein’s “client list.” While the FBI may or may not have developed a “client list” per se, they most certainly did develop Analyst Notebook Charts surrounding Epstein. If done correctly using sufficient information, the charts would include both the clients and suppliers of the international child sex trafficking network.
Although the FBI reportedly assigned over 1,000 FBI employees to review the so-called “Epstein Files,” it is unclear if these files contained the FBI’s own i2 charts of this network. The public and Congress have no way to confirm if the charts were included in the “Epstein Files” that Pam Bondi demanded from the FBI.
Founded in Cambridge England in 1990, i2 Group produced software for “visual intelligence and investigative analysis software for private and public intelligence agencies.” It appears to have incorporated artificial intelligence at some point. Palantir later stole i2’s code. Apparently the FBI used this software in 2006 while investigating Jeffrey Epstein.
According to FBI files released in 2019, the FBI created a total of 16 charts using this software. I assume that the “charts” are a visual depiction of the network using the names of individuals and lines drawn between them.
“Charts” are described by i2 below.
Charts
Charts display the intelligence that relates to an investigation. You can create charts both manually and automatically by using information from various sources. This information might be personal knowledge, written reports, photographs, video clips, spreadsheets, email, word-processing files, and databases.
The image below is from an i2 tutorial, showing what a chart could look like.
More on i2 Analyst’s Notebook from i2:
The advanced visual analysis solution for investigators to combat fraud and crime.
With i2® Analyst’s Notebook®, users gain rich visual analysis capabilities that quickly turn complex sets of disparate information into high-quality, actionable intelligence to help them and those involved in intelligence analysis identify, predict, and counter criminal, terrorist and fraudulent activities.
Designed to help government agencies and private sector businesses in their fight against increasingly sophisticated criminal and terrorist organizations, Analyst’s Notebook has been relied upon for more than 30 years by over 2,000 organizations worldwide. Get in touch today for an i2 Analyst's Notebook demo.
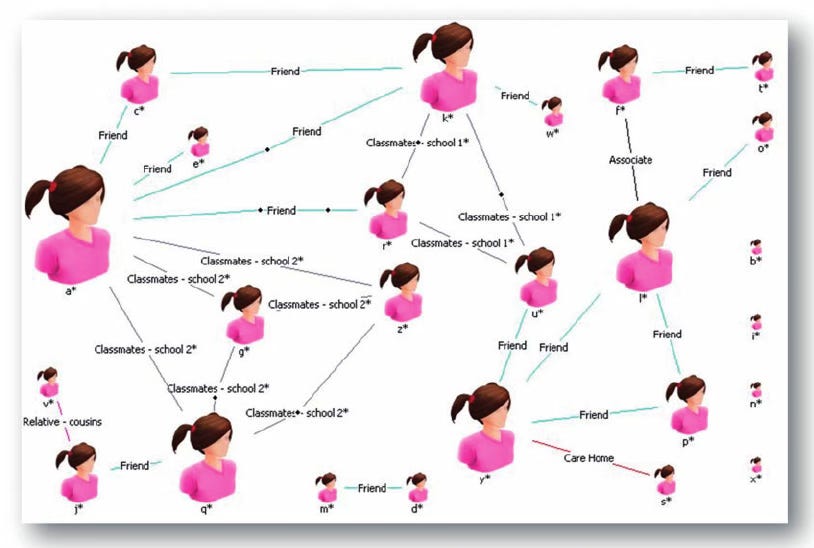
i2 has been used extensively to pattern child sex trafficking networks. The image below was titled “Operation X Victim Network” in a paper titled “Exploring Internal Child Sex Trafficking Networks Using Social Network Analysis,” 2011.
Excerpt:
Police have enjoyed a long history of mapping connections between actors and commodities involved in crime (Borgatti et al., 2009), particularly organized crime, in line with initiatives such as Organized Crime Group (OCG) mapping. Generally, networks are built with data from ongoing investigations and focus on offenders. The hand-drawn network charts once found on the walls of operation rooms have given way to their computerized equivalent. All UK police forces now use i2 Analyst’s Notebook, a dedicated SNA software package with in-built centrality metrics, used by private security firms and law enforcement across the world, including America’s FBI (Wakefield, 2003).
Keep reading with a 7-day free trial
Subscribe to C’s Newsletter to keep reading this post and get 7 days of free access to the full post archives.